In the digital age, cybersecurity is a critical concern for businesses of all sizes. The stakes are particularly high for small—to medium-sized companies in Northeast Ohio. Without the technical expertise to manage IT infrastructure, these businesses are often vulnerable to cyber threats. This article sheds light on two key strategies: reactive vs proactive cybersecurity in Northeast Ohio.
We’ll explore each’s benefits and limitations and provide practical solutions for improving your business’s cybersecurity in Northeast Ohio.
Understanding Cybersecurity in Northeast Ohio
Cybersecurity is the practice of protecting systems, networks, and data from digital attacks and data breaches. These attacks often aim to access, change, or destroy sensitive information. Understanding cybersecurity is crucial for small businesses in Northeast Ohio.
Here’s why:
- Cyber threats are evolving and becoming more sophisticated.
- Small businesses often lack the resources to recover from a cyber attack.
- Cyber attacks can lead to significant financial loss and damage to reputation.
The Current Cybersecurity Landscape
The cybersecurity landscape in Northeast Ohio is diverse. It’s home to a mix of small businesses across various industries, each with unique cybersecurity needs.
However, the common thread is the need for robust cybersecurity strategies to protect against ever-evolving threats.
Why SmBs are a Target
Cybercriminals often view small businesses as easy targets because they may lack the resources or expertise to implement comprehensive cybersecurity measures.
Moreover, a successful attack can give cybercriminals access to sensitive data, making small businesses a lucrative target.
Reactive Approach To Cybersecurity
Reactive cybersecurity is a strategy that responds to threats after they occur.
It involves identifying, containing, eliminating the threat, and recovering from the attack.
While this approach can be effective, it often results in downtime and potential data loss.
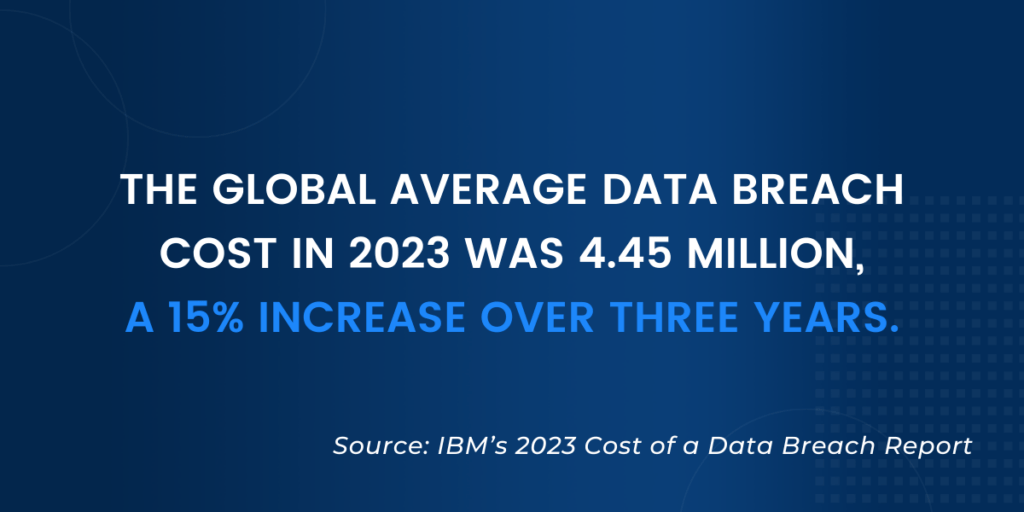
The Cost of Reactive Cyber Security
The cost of a cyber attack can be significant for small businesses. This includes the financial cost of recovery and the potential loss of customer trust.
Moreover, the time and resources spent on recovery can divert attention from core business activities.
Proactive Approach To Cybersecurity
Proactive strategies, on the other hand, involves identifying potential threats before they happen. This approach involves real-time monitoring, regular risk assessments, and the implementation of network security measures.
Proactive cybersecurity is about creating a security culture within your business and staying informed about the latest threats.
Investing in Prevention: Long-term Benefits of Proactive Cybersecurity Strategies
While proactive cybersecurity may require an upfront investment, it can lead to long-term cost savings. By preventing breaches, you avoid the costs associated with recovery and damage control.
Moreover, a proactive approach can enhance your business reputation, building trust with customers and partners.
Proactive Measures to Implement
Several proactive measures can be implemented to enhance your cybersecurity.
Proactive Cybersecurity Includes:
- regular software updates
- employee cybersecurity education
- strong password policies
- and multi-factor authentication.
Also, consider implementing a cybersecurity incident response plan and investing in cybersecurity insurance.
Finally, continuous monitoring and threat detection systems can help avoid potential threats.
[Related: Cybersecurity Travel Tips: Secure Personal Devices On The Go]
Comparing Proactive vs Reactive Cybersecurity
When comparing reactive and proactive cybersecurity, it’s clear that both approaches have their merits.
Reactive cybersecurity is essential for responding to threats and minimizing damage when they occur.
On the other hand, proactive cybersecurity can prevent threats from occurring in the first place, saving your business from potential losses and reputation damage.
- Reactive Cybersecurity: Responds to threats after they occur, minimizing damage and recovery time.
- Proactive Cybersecurity: Anticipates and prevents threats, saving potential losses and reputation damage.
Balancing the Approaches for Your Northeast Ohio Business
The key is to balance the two approaches that suit your business.
This will depend on factors such as your business size, industry, and the nature of the data you handle.
Ultimately, a combination of reactive and proactive measures will provide the most comprehensive protection for your business.
Practical Solutions for Small Business Owners
As a small business owner, you might feel overwhelmed by the complexity of cybersecurity. But don’t worry; there are practical solutions you can implement to protect your business.
These include creating a cybersecurity policy, conducting regular training, and staying informed about the latest threats.
Here are some steps you can take:
- Conduct a risk assessment to identify vulnerabilities.
- Implement strong password policies and multi-factor authentication.
- Regularly update and patch your software.
- Install a reliable firewall and intrusion prevention system.
- Back up your data regularly and store it securely.
- Team up with a Managed IT and Security Services partner to handle the legwork.
Creating a Cybersecurity Policy
A cybersecurity policy is a must for every business.
It outlines the steps your business will take to protect its information assets.
This policy should be clear, comprehensive, and regularly updated to reflect the changing cybersecurity landscape.
Regular Training and Awareness Programs
Training is a crucial part of cybersecurity.
Your employees need to understand the risks and how to avoid them.
Regular training and awareness programs can help them stay vigilant against threats.
Conclusion | Reactive vs Proactive Cybersecurity in Northeast Ohio
In the end, the choice between reactive and proactive cybersecurity in Northeast Ohio is not binary. It’s about finding the right balance that suits your business needs and resources.
Remember, the goal is to protect your business, its data, and its reputation. So, prioritize cybersecurity and invest in the right strategies and partnerships.
