Spot The Smish | Interactive Blog Challenge

Can You Spot The Smishing Attempt?
Try our interactive blog challenge and sharpen your skills in identifying smishing attempts!
1. Smish or Legit?
Choose your answer below.
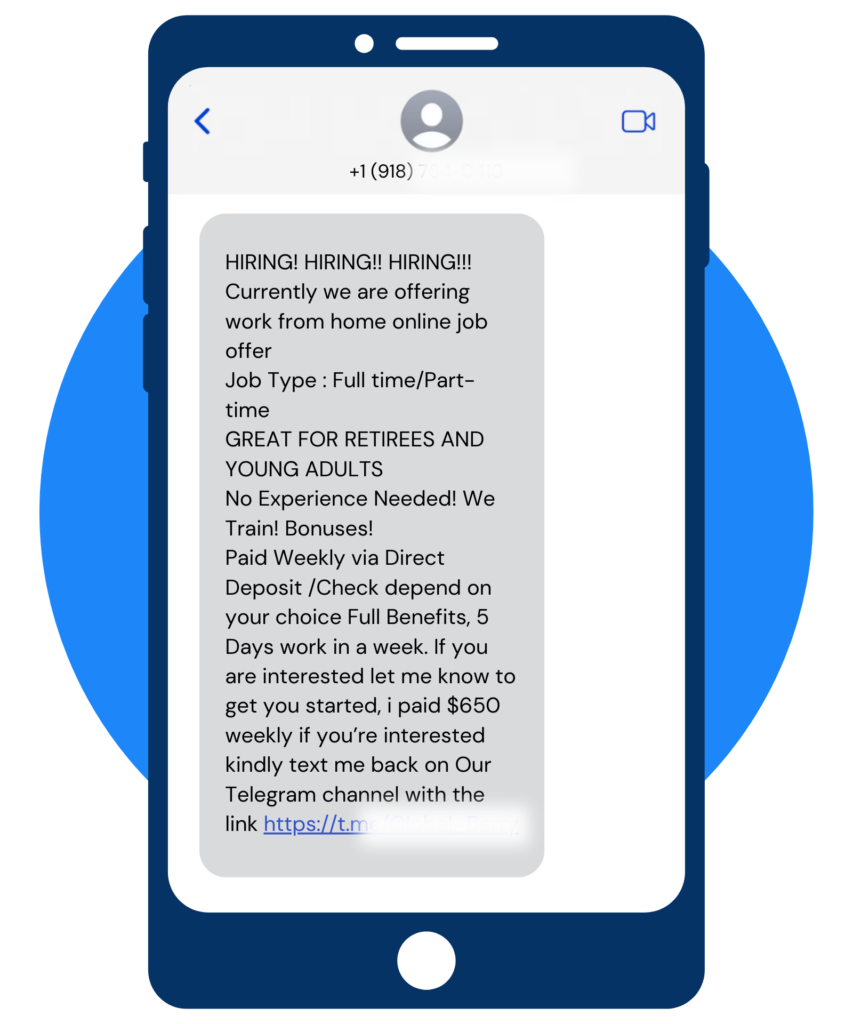
Smishing Attempt
You’re correct– Great job!
Signs that this is a smishing attempt:
- Overly Aggressive Tactics: The use of “HIRING HIRING HIRING” in all caps and repeated multiple times is designed to grab attention immediately. Legitimate companies typically do not need to resort to such aggressive tactics to fill their positions.
- Too Good to Be True: As the old saying goes, if something seems too good to be true, it probably is. Offers that promise high pay for minimal work, especially with no experience required, are often bait used by scammers to lure in targets.
- Urgency: These messages may create a sense of urgency, suggesting that the opportunity is limited and you must act fast. This pressure tactic is a common strategy in phishing attempts to prompt quick action without giving the recipient time to think critically or investigate the legitimacy of the offer.
- Suspicious Links: The message may include links asking you to apply through them. These links could lead to fraudulent websites that steal personal information or infect devices with malware. Legitimate job offers usually direct candidates to apply through well-known job boards or the company’s official website.
- Lack of Details: The message might be vague about the job role, company name, or specific responsibilities. Genuine job offers provide sufficient detail about the position and the company to allow candidates to research and verify the opportunity.
- Unprofessional Presentation: Look out for spelling and grammatical errors, which can indicate a lack of professionalism and suggest the message is not from a legitimate source.
Legit Message
Incorrect– This is a smishing attempt!
Signs that this is a smishing attempt:
- Overly Aggressive Tactics: The use of “HIRING HIRING HIRING” in all caps and repeated multiple times is designed to grab attention immediately. Legitimate companies typically do not need to resort to such aggressive tactics to fill their positions.
- Too Good to Be True: As the old saying goes, if something seems too good to be true, it probably is. Offers that promise high pay for minimal work, especially with no experience required, are often bait used by scammers to lure in targets.
- Urgency: These messages may create a sense of urgency, suggesting that the opportunity is limited and you must act fast. This pressure tactic is a common strategy in phishing attempts to prompt quick action without giving the recipient time to think critically or investigate the legitimacy of the offer.
- Suspicious Links: The message may include links asking you to apply through them. These links could lead to fraudulent websites that steal personal information or infect devices with malware. Legitimate job offers usually direct candidates to apply through well-known job boards or the company’s official website.
- Lack of Details: The message might be vague about the job role, company name, or specific responsibilities. Genuine job offers provide sufficient detail about the position and the company to allow candidates to research and verify the opportunity.
- Unprofessional Presentation: Look out for spelling and grammatical errors, which can indicate a lack of professionalism and suggest the message is not from a legitimate source.

2. Smish or Legit?
Choose your answer below.
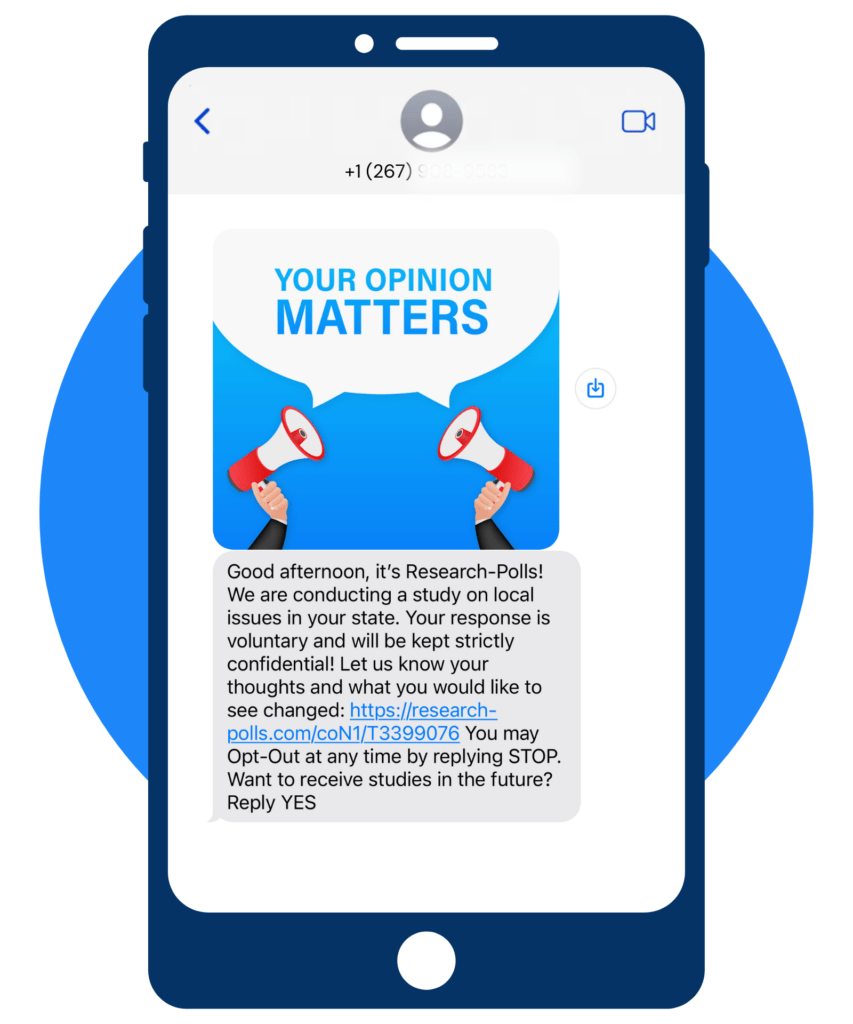
Smishing Attempt
You’re correct– Great job!
Signs that this is a smishing attempt:
- Unsolicited Link: Including a link in a text message, especially from an unknown or unverified source, is a common hallmark of scamming attempts. Legitimate organizations typically don’t ask you to click on links without prior context or consent.
- Presence of an Image: The use of an image, mainly if it appears to be legitimate or official, can be a tactic to lend credibility to the message. However, images can also be misleading and used to evoke an emotional response, encouraging hasty actions without proper verification.
- Lack of Personalization: Legitimate communications from political organizations or pollsters often include some level of personalization, such as addressing the recipient by name. A generic message could indicate a smishing attempt, targeting a broad audience and hoping to trick a few.
- Request for Confidential Information: If the link leads to a request for personal or confidential information, it’s a clear sign of a smishing attempt. Legitimate polls and political inquiries will rarely, if ever, ask for sensitive data via text message links.
- Previous Communication: If you have not signed up for political updates or polls, receiving such a message out of the blue is suspicious. Legitimate organizations typically communicate through these channels only with prior consent.
Legit Message
Incorrect– This is a smishing attempt!
Signs that this is a smishing attempt:
- Unsolicited Link: Including a link in a text message, especially from an unknown or unverified source, is a common hallmark of scamming attempts. Legitimate organizations typically don’t ask you to click on links without prior context or consent.
- Presence of an Image: The use of an image, mainly if it appears to be legitimate or official, can be a tactic to lend credibility to the message. However, images can also be misleading and used to evoke an emotional response, encouraging hasty actions without proper verification.
- Lack of Personalization: Legitimate communications from political organizations or pollsters often include some level of personalization, such as addressing the recipient by name. A generic message could indicate a smishing attempt, targeting a broad audience and hoping to trick a few.
- Request for Confidential Information: If the link leads to a request for personal or confidential information, it’s a clear sign of a smishing attempt. Legitimate polls and political inquiries will rarely, if ever, ask for sensitive data via text message links.
- Previous Communication: If you have not signed up for political updates or polls, receiving such a message out of the blue is suspicious. Legitimate organizations typically communicate through these channels only with prior consent.

3. Smish or Legit?
Choose your answer below.
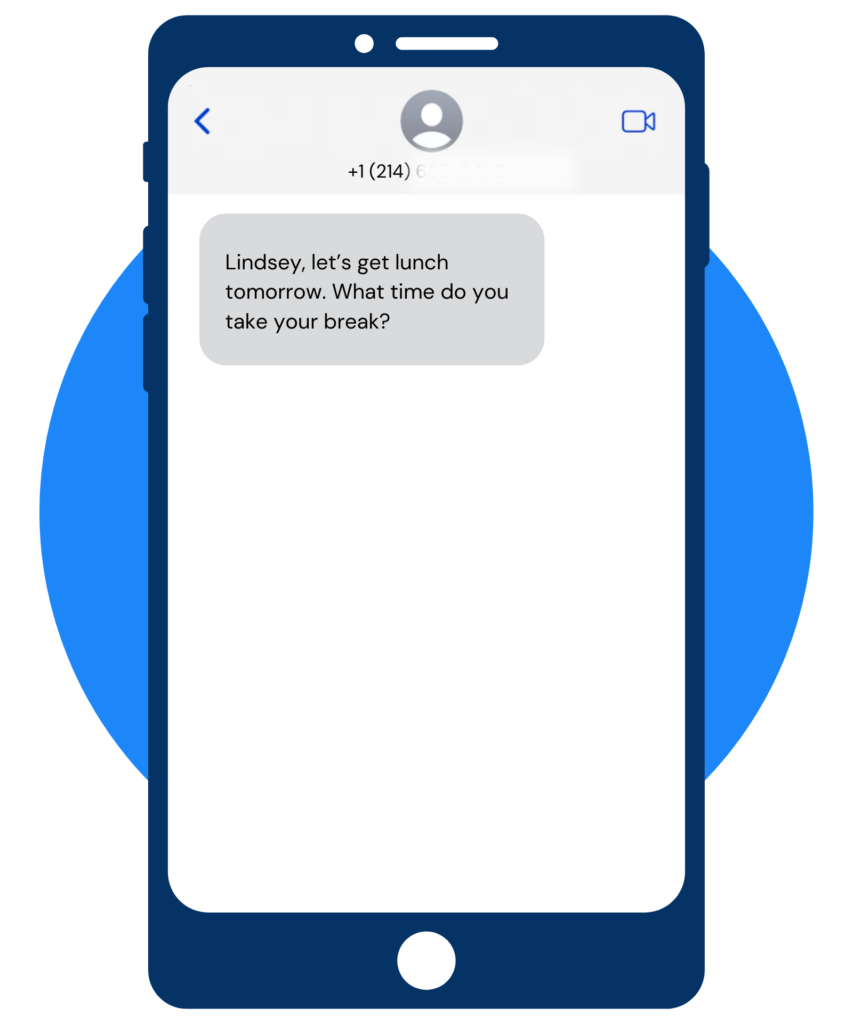
Smishing Attempt
You’re correct– Great job!
Signs that this is a smishing attempt:
- Lack of Personalization: Legitimate messages, especially from contacts who know you well enough to invite you out to lunch, will use your correct name. A message with the wrong name suggests it’s a generic attempt sent to multiple recipients, hoping someone will respond.
- Generic Phrasing: Alongside the incorrect name, the content might use vague or generic phrasing. This indicates the sender does not know you personally, contrary to the implied familiarity of an invite to lunch.
- Unfamiliar Sender Information: If the message comes from an unknown number or email address, it’s a red flag. Scammers often use spoofed numbers or email addresses that appear similar to legitimate contacts but are slightly altered.
- Attempts to Establish Trust: By pretending to be someone you might know (albeit getting the name wrong), the sender attempts to bypass your initial defenses. This is a manipulative technique aimed at creating a false sense of security.
- Inconsistency with Known Patterns: If you typically don’t receive lunch invitations in this manner or the message shifts from the usual communication style of the person it’s purportedly from, trust your instincts that something might be off.
Legit Message
Incorrect– This is a smishing attempt!
Signs that this is a smishing attempt:
- Lack of Personalization: Legitimate messages, especially from contacts who know you well enough to invite you out to lunch, will use your correct name. A message with the wrong name suggests it’s a generic attempt sent to multiple recipients, hoping someone will respond.
- Generic Phrasing: Alongside the incorrect name, the content might use vague or generic phrasing. This indicates the sender does not know you personally, contrary to the implied familiarity of an invite to lunch.
- Unfamiliar Sender Information: If the message comes from an unknown number or email address, it’s a red flag. Scammers often use spoofed numbers or email addresses that appear similar to legitimate contacts but are slightly altered.
- Attempts to Establish Trust: By pretending to be someone you might know (albeit getting the name wrong), the sender attempts to bypass your initial defenses. This is a manipulative technique aimed at creating a false sense of security.
- Inconsistency with Known Patterns: If you typically don’t receive lunch invitations in this manner or the message shifts from the usual communication style of the person it’s purportedly from, trust your instincts that something might be off.

4. Smish or Legit?
Choose your answer below.
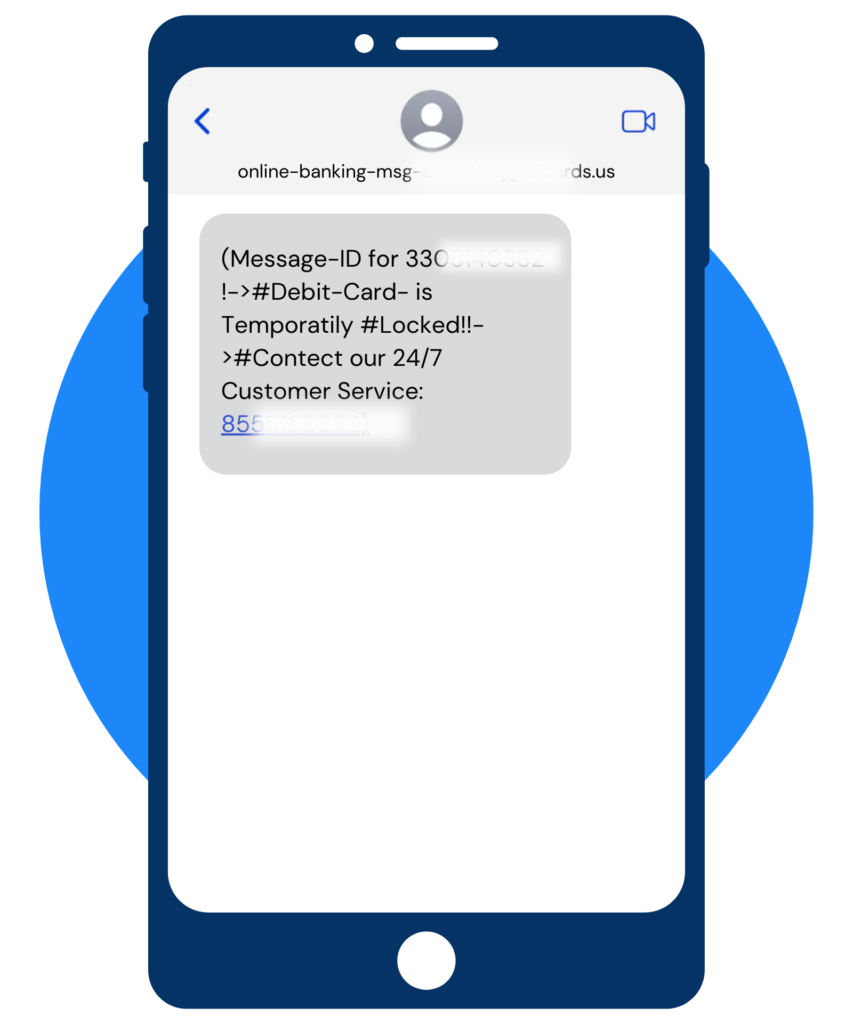
Smishing Attempt
You’re correct– Great job!
Signs that this is a smishing attempt:
- Urgency and Pressure: If the message claims that your card is locked and demands immediate action, it’s employing a common tactic used in smishing attempts. Banks typically use more formal channels for urgent communications and provide a clear, secure path to resolve issues without pressuring you for quick, uninformed actions.
- Suspicious Links: The message includes a link asking you to unlock your card or verify your identity. Legitimate banks encourage customers to log into their accounts through official apps or websites they have previously used, not links in unsolicited messages.
- Generic Greeting: The message doesn’t address you by your full name or uses a generic greeting such as “Dear customer.” Banks usually personalize communications with your name to confirm the message’s legitimacy.
- Lack of Official Bank Contact Information: Legitimate messages from your bank typically include official contact information for customer service, encouraging you to reach out through known, secure channels if you have concerns. A smishing attempt might lack this or provide fake contact details.
- Threats or Consequences: If the message threatens severe consequences, such as legal action or financial loss, if you don’t respond immediately, it’s likely a scare tactic used in smishing schemes. Banks communicate account issues in a more measured and professional manner.
- Previous Communication: If you haven’t received any prior notification from your bank through recognized channels (like an official app notification or a call from a known bank number) about issues with your card, a sudden, urgent text message is suspicious
Legit Message
Incorrect– This is a smishing attempt!
Signs that this is a smishing attempt:
- Urgency and Pressure: If the message claims that your card is locked and demands immediate action, it’s employing a common tactic used in smishing attempts. Banks typically use more formal channels for urgent communications and provide a clear, secure path to resolve issues without pressuring you for quick, uninformed actions.
- Suspicious Links: The message includes a link asking you to unlock your card or verify your identity. Legitimate banks encourage customers to log into their accounts through official apps or websites they have previously used, not links in unsolicited messages.
- Generic Greeting: The message doesn’t address you by your full name or uses a generic greeting such as “Dear customer.” Banks usually personalize communications with your name to confirm the message’s legitimacy.
- Lack of Official Bank Contact Information: Legitimate messages from your bank typically include official contact information for customer service, encouraging you to reach out through known, secure channels if you have concerns. A smishing attempt might lack this or provide fake contact details.
- Threats or Consequences: If the message threatens severe consequences, such as legal action or financial loss, if you don’t respond immediately, it’s likely a scare tactic used in smishing schemes. Banks communicate account issues in a more measured and professional manner.
- Previous Communication: If you haven’t received any prior notification from your bank through recognized channels (like an official app notification or a call from a known bank number) about issues with your card, a sudden, urgent text message is suspicious

5. Smish or Legit?
Choose your answer below.
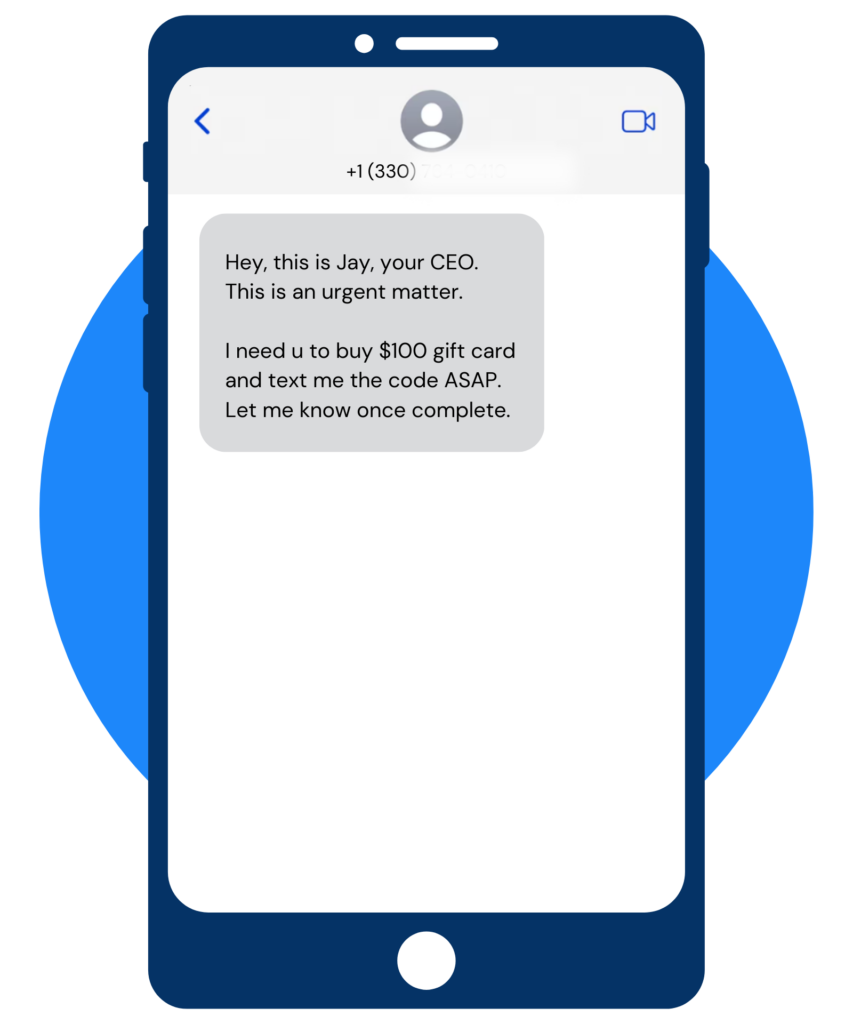
Smishing Attempt
You’re correct– Great job!
Signs that this is a smishing attempt:
- Poor Spelling and Grammar: Professional messages from legitimate companies are usually well-written. Messages that contain noticeable spelling and grammar mistakes could be a sign of a smishing attempt.
- Unusual Request: It’s highly unlikely for a CEO or any high-ranking official of a company to request employees to purchase gift cards directly. Such requests don’t align with standard corporate communication or procurement procedures.
- Suspicious Sender Information: If the message comes from an email address or phone number that doesn’t match the company’s official communication channels, it’s a strong scam indicator. Legitimate messages from your CEO would come from known, verified sources.
- Urgency or Threats: The message might create a sense of urgency, pressuring you to act quickly. This tactic is designed to prevent you from thinking critically or verifying the request. Authentic requests from company leadership usually follow formal channels and allow time for verification.
- No Prior Communication: If the request comes out of the blue without prior discussion or announcement, it’s suspicious. Genuine tasks or requests of this nature would typically be discussed through official meetings or documented communications.
Legit Message
Incorrect– This is a smishing attempt!
Signs that this is a smishing attempt:
- Poor Spelling and Grammar: Professional messages from legitimate companies are usually well-written. Messages that contain noticeable spelling and grammar mistakes could be a sign of a smishing attempt.
- Unusual Request: It’s highly unlikely for a CEO or any high-ranking official of a company to request employees to purchase gift cards directly. Such requests don’t align with standard corporate communication or procurement procedures.
- Suspicious Sender Information: If the message comes from an email address or phone number that doesn’t match the company’s official communication channels, it’s a strong scam indicator. Legitimate messages from your CEO would come from known, verified sources.
- Urgency or Threats: The message might create a sense of urgency, pressuring you to act quickly. This tactic is designed to prevent you from thinking critically or verifying the request. Authentic requests from company leadership usually follow formal channels and allow time for verification.
- No Prior Communication: If the request comes out of the blue without prior discussion or announcement, it’s suspicious. Genuine tasks or requests of this nature would typically be discussed through official meetings or documented communications.

You’ve Completed our ‘Spot the Smish’ interactive blog challenge!
We hope this challenge has not only been engaging but has also equipped you with the knowledge to recognize and respond to phishing attempts confidently.
Keep practicing what you’ve learned and share this knowledge with others. Cybersecurity is a shared responsibility, and together, we can create a safer digital world for everyone.
Stay safe and keep the conversation about cybersecurity going!