noun phish·ing | ˈfi-shiŋ
Phishing is a cyber-attack where cybercriminals use deceptive emails, text messages, or phone calls to extract confidential information from individuals or organizations. They often disguise themselves as legitimate entities to gain victims’ trust and exploit their data.
The consequences of phishing attacks can be devastating, including financial loss and damage to reputations. Understanding what phishing is, how it works and taking preventative measures to protect yourself and your business from these cyber threats is essential.
Phishing Attack Statistics
- 91% of cyber attacks begin with a phishing email.
- The global average cost of a data breach in 2023 was 4.45 million, a 15% increase since 2020.
- 1 in 3 organizations click on links in phishing emails, and 12% of those links lead to malware.
- 97% of people are unable to identify a sophisticated phishing email.
- Small businesses face 43% of cyber attacks.
- Finance and Insurance industries are the most targeted sectors for phishing attacks.
- Phishing attackers aim to steal login credentials in 35% of attacks.

The History of Phishing
Phishing has been a persistent threat to individuals and organizations since the mid-1990s. Initially, attempts were simple and easy to identify, often involving poorly crafted emails with obvious spelling and grammar mistakes.
However, as technology advanced and users became more aware of these tactics, hackers adapted and refined their techniques.
Today, phishing attacks have become increasingly difficult to detect. Cybercriminals employ various strategies to trick individuals into divulging sensitive information. These tactics often involve creating compelling emails, text messages, or even phone calls that appear to be from legitimate sources, making it challenging for recipients to distinguish them from genuine communications.
How to Spot a Phishing Email
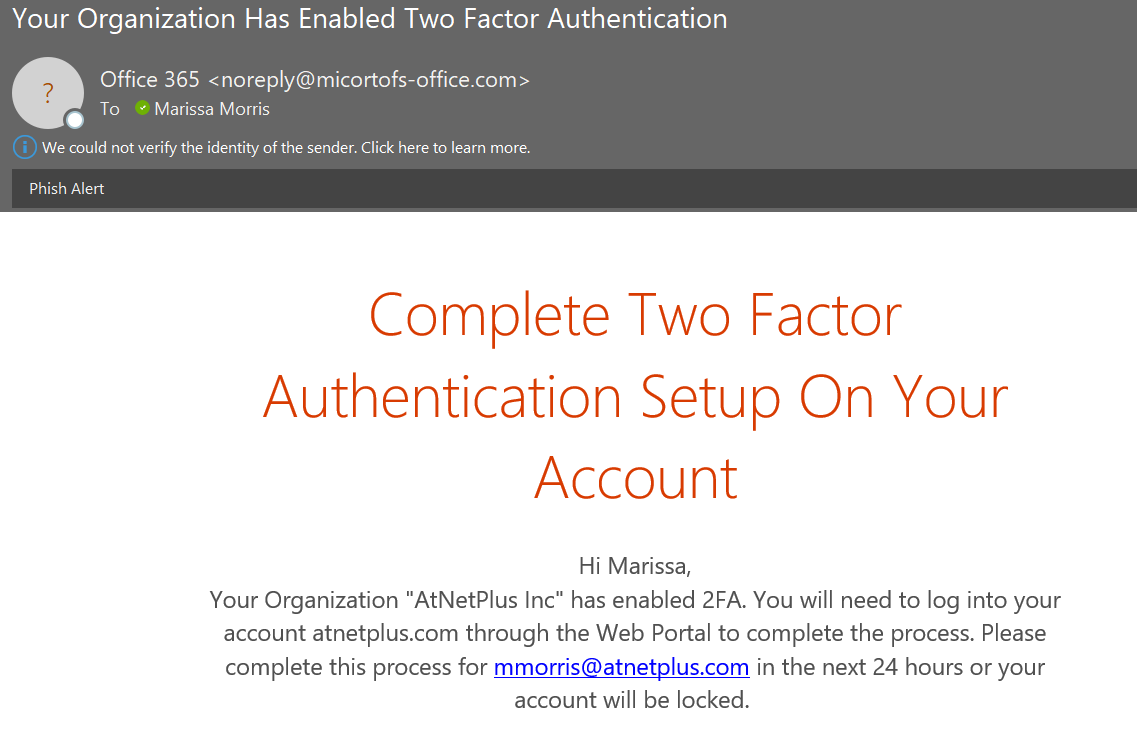
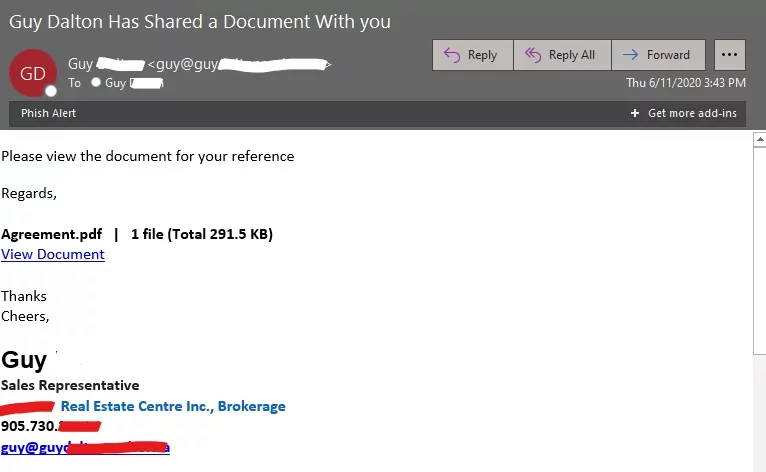
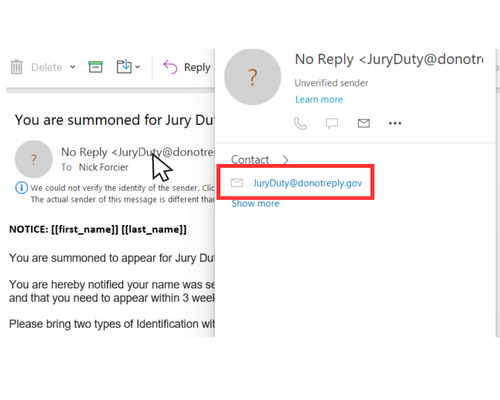
1. CHECK THE SENDER’S EMAIL ADDRESS:
Cybercriminals often use email addresses that are similar to legitimate ones but with slight variations. Look out for misspellings, added numbers, or different domain names.
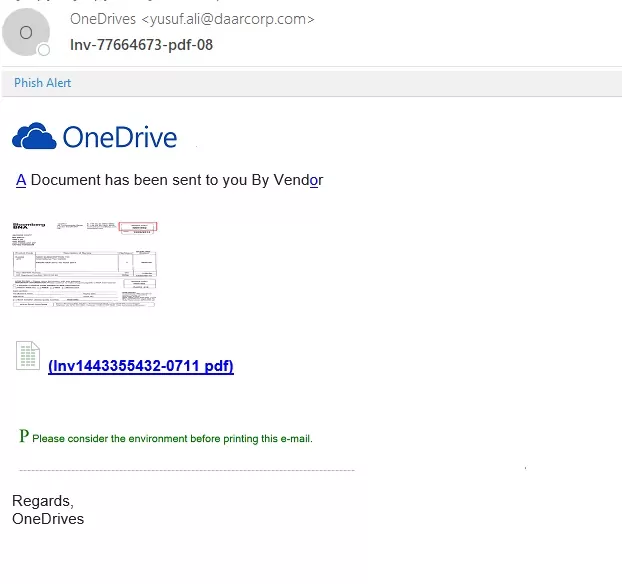
2. LOOK FOR GRAMMATICAL ERRORS:
Phishing emails often have spelling and grammar mistakes because creators usually make them quickly and do not proofread.
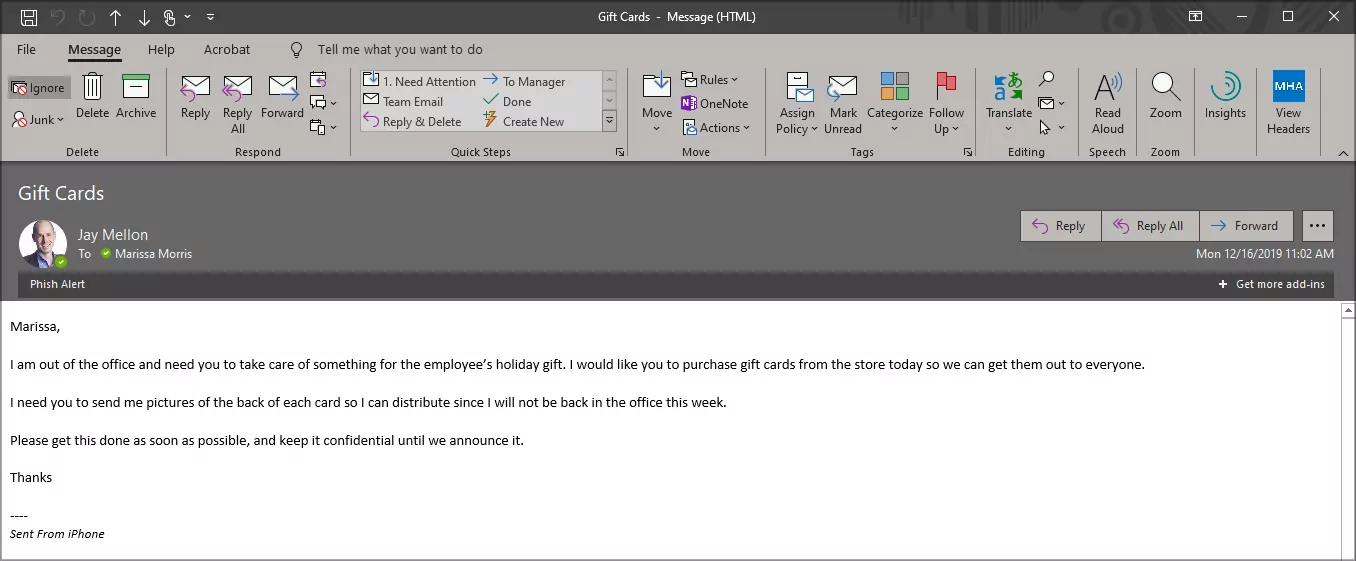
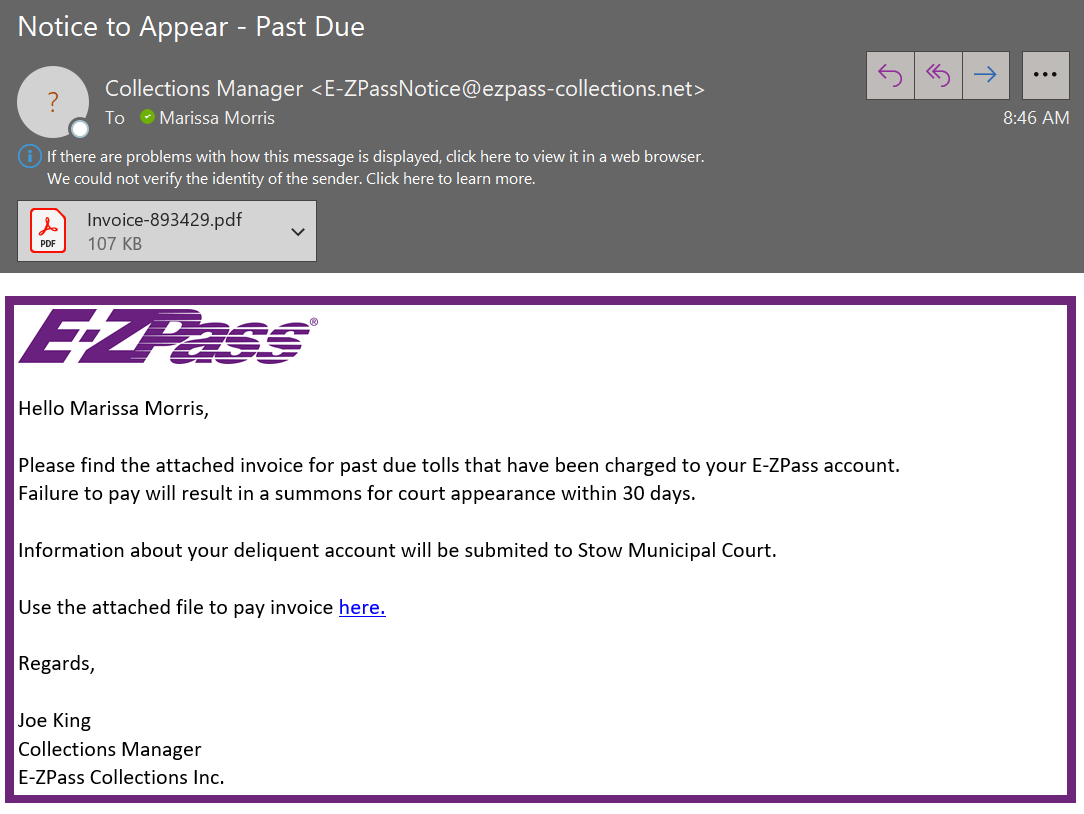
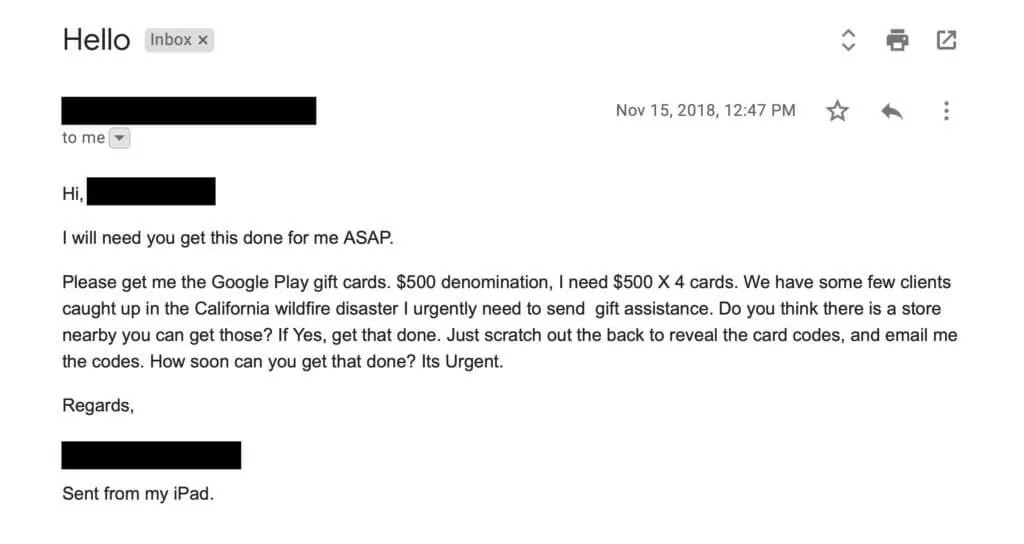
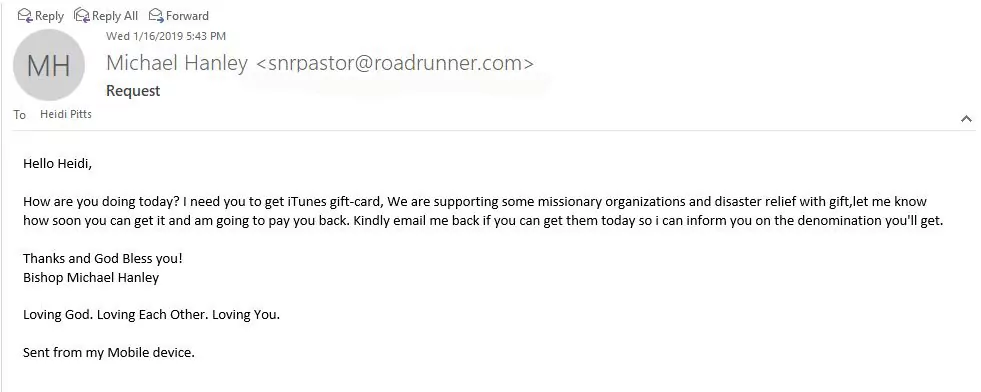
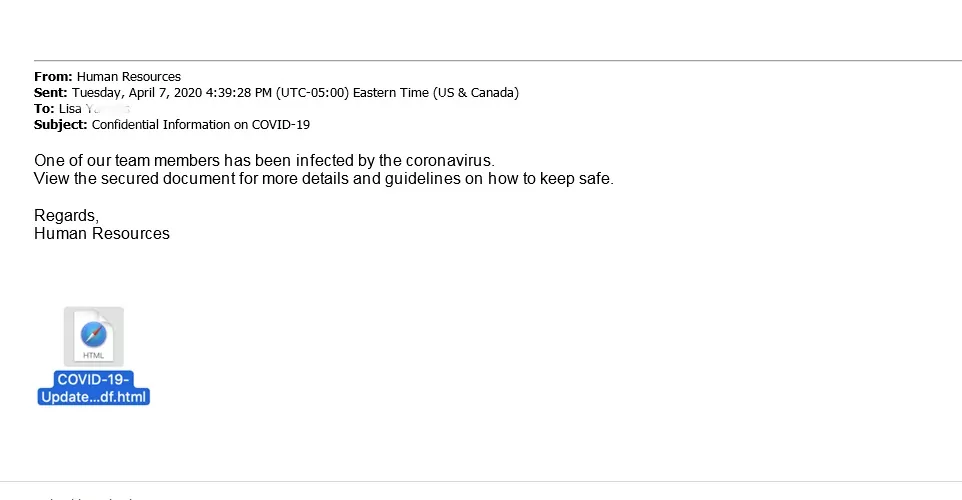
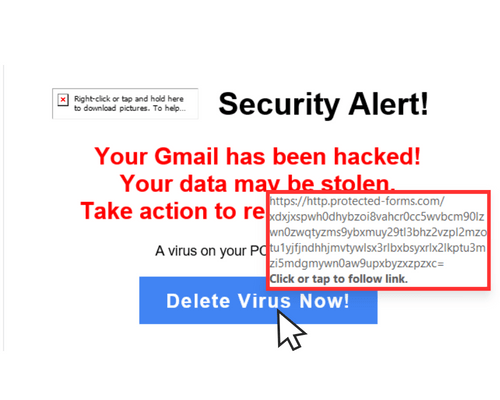
3. CHECK FOR SENSE OF URGENCY:
Phishing emails often contain urgent requests or threats, urging you to act quickly without thinking.

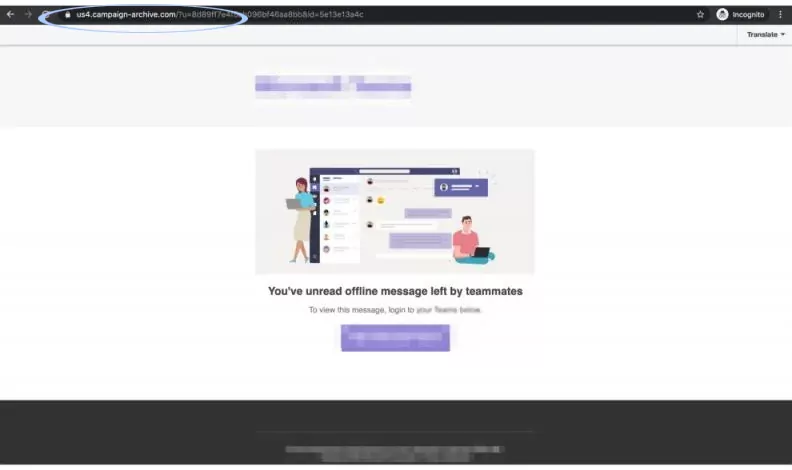
4. HOVER OVER LINKS:
Before clicking any links, hover your mouse over them to see if the URL matches the sender’s domain name. Be wary of shortened links or links that redirect you to a different website.
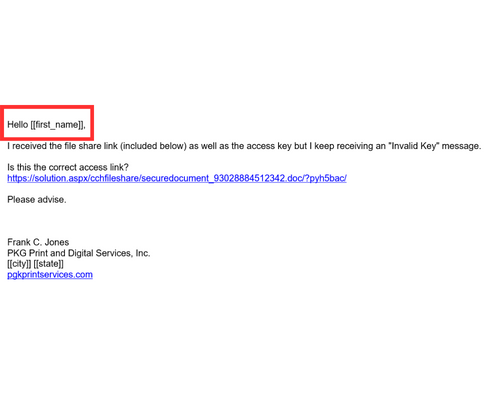
5. CHECK THE SALUTATION AND CONTENT:
Phishing emails often use generic salutations such as “Dear customer” instead of addressing you by name. They may also contain content irrelevant to you or unrelated to the sender.
What are the consequences of falling victim to a Phishing attack?
The consequences of falling victim to an attack can be severe and far-reaching. Financial loss is one of the most common outcomes, as cybercriminals can use stolen information to access bank accounts or make fraudulent purchases.
In addition, phishing attacks can lead to identity theft, reputational damage, and compromised cybersecurity. Individuals and organizations may also face legal or regulatory consequences if they fail to protect sensitive data adequately.
Preventative Cybersecurity Measures
EDUCATION AND AWARENESS
Today’s tools are incredibly helpful in protecting and identifying threats after they occur, but human error is the number one cause for successful scam attempts on businesses.
Educating yourself about the latest phishing techniques and staying informed about common scams can also go a long way. By being aware of the tactics scammers use and staying cautious when it comes to sharing personal information online, you can significantly reduce the risk of falling victim to phishing scams. Additionally, it is crucial to keep software and security systems up to date, as they can help detect and prevent phishing attempts.
INVEST IN ROBUST SECURITY MEASURES
To safeguard your business, investing in robust cybersecurity tools such as firewalls, anti-virus/anti-malware software, and Phishing Identification and Remediation is recommended. These proactive measures can significantly reduce the risks of successful scams and minimize your organization’s vulnerability to cyber threats.
IMPLEMENT MULTI-FACTOR AUTHENTICATION (MFA)
Adding Multi-Factor Authentication to your login process can provide an additional and vital layer of security. By requiring a second form of authentication, such as a fingerprint scan or a code sent to a mobile device, MFA can significantly reduce the risk of unauthorized access to sensitive information.
[Related: Is Your Northeast Ohio Business Suffering from MFA Fatigue?]
KEEP ALL SOFTWARE UP-TO-DATE
Keeping software updated is crucial to protect against cyber threats. Regular updates and security patches can prevent attackers from exploiting vulnerabilities.
BE CAUTIOUS OF LINKS AND ATTACHMENTS
It is important to be cautious when clicking on links or opening attachments from unknown sources. Cybercriminals often use links and attachments to spread malware or gain access to sensitive information.
Therefore, it’s important to verify that the links and attachments are legitimate and from a trusted source before clicking on them or downloading them. If you are unsure about the legitimacy of the link or attachment, do not click on it or open it. Instead, contact the sender and ask for verification before proceeding.
BE CAUTIOUS ABOUT SHARING PERSONAL INFORMATION ONLINE
Cybercriminals often use social engineering techniques to trick individuals into divulging sensitive information. You and your team must be careful about the information shared online and avoid sharing sensitive data, including financial information and personal details.
Conclusion | What is Phishing?
By understanding and actively defending against phishing attacks, you are taking a crucial step in safeguarding your personal and organizational data. Implementing the preventive measures we have outlined can significantly reduce the risk of falling victim to these malicious schemes. Remember, education and vigilance are your best defenses against phishing.
Ready for a security boost? Protect your business from threats like phishing with AtNetPlus Managed IT and Security Services.