If you’ve ever tapped “Yes, it’s me” on a login notification without a second thought, you’re not alone. Multi-factor Authentication (MFA) has become a normal part of our digital lives. But there’s a threat that’s taking advantage of our habits— and it’s called a MFA fatigue attack.
Let’s break down what MFA is, why it matters, and how this growing cyberattack trend could impact you or your Northeast Ohio business.
What Is MFA (Multifactor Authentication)?
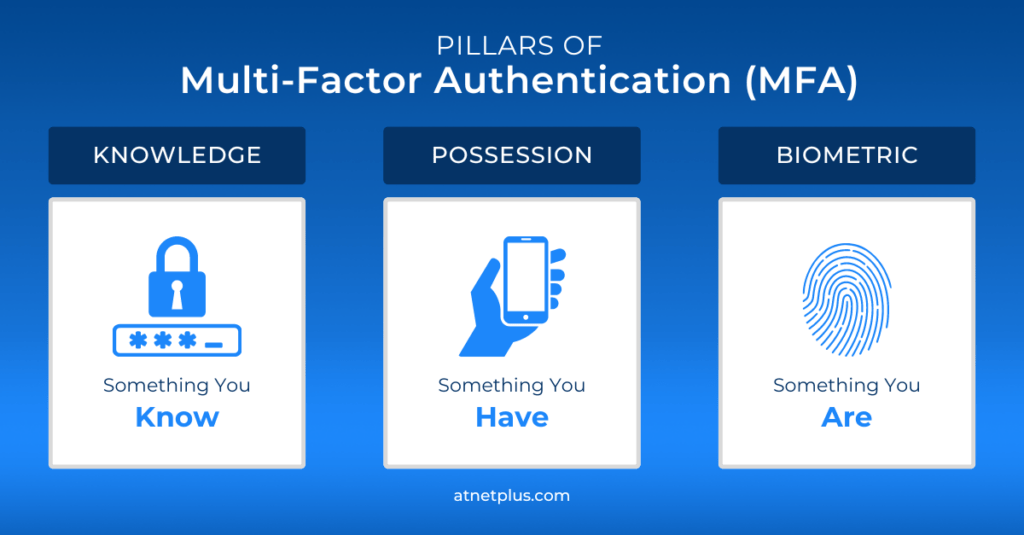
Multifactor authentication (MFA) is a security measure that requires users to verify their identity using two or more methods before accessing an account or system. It provides an additional level of security beyond a username and password.
Here’s how it typically works:
- Something you know — like a password or PIN
- Something you have — like a smartphone or security token
- Something you are — like a fingerprint or face scan
A common example? You log into your email with a password, then get a push notification on your phone asking you to approve the login. That second step is your MFA.
Multi-factor authentication is one of the most effective ways to stop cybercriminals, but only if users are paying attention.
So, What Is MFA Fatigue?
MFA fatigue (also known as MFA prompt bombing or push fatigue) happens when users receive repeated login prompts and eventually approve one out of annoyance or habit.
Cybercriminals exploit this by:
- Trying to log in repeatedly with stolen credentials
- Flooding the real user with notifications
- Waiting for them to hit “approve” just to stop the buzzing
It’s social engineering, but automated.
And it works. Once that user taps “approve,” the attacker is in.
Why MFA Fatigue Is a Big Deal for Businesses
Whether you’re running a small business in Akron, managing remote teams in Canton, or securing a growing operation in Cleveland, MFA is probably part of your cybersecurity setup.
But here’s the catch: when MFA requests become routine, it becomes risky. If employees approve prompts without thinking, cybercriminals can slip in undetected.
MFA fatigue is now one of the most common techniques in real-world breaches, including several high-profile incidents involving well-known companies.
Real-World Example: MFA Fatigue Used in Hawaiian Airlines Breach
A recent cyberattack in June 2025 shows just how dangerous MFA fatigue has become— even for large, well-resourced companies.
Hawaiian Airlines was targeted by the cybercriminal group Scattered Spider, which used a combination of phishing and MFA fatigue techniques to break into internal systems. After stealing login credentials, the attackers flooded the victim with push notifications, hoping they’d eventually approve one out of frustration or confusion.
And it worked.
Once the user clicked “approve,” the attackers gained access– all without needing to bypass traditional cybersecurity defenses.
This breach is a clear reminder that MFA alone isn’t enough if users aren’t trained and your systems don’t include additional protections like number matching, biometric prompts, or login context.
If it can happen to a major airline, it can happen to any business– especially if attackers think your team might fall for a push notification blitz.

How to Know If You’re at Risk
Keep an eye out for:
- Team members saying “I just click approve automatically”
- Multiple MFA push notifications sent outside of business hours
- No protections in place beyond basic push notifications
- A lack of employee education around what to do when they get suspicious requests
How to Protect Your Business from MFA Fatigue
Here are practical steps to strengthen your security posture:
Educate your users.
Help your team understand that every prompt should be treated seriously. If something feels off, they shouldn’t approve it.
Use smarter MFA methods.
Tools like number matching or biometric prompts make it harder for attackers to fake or flood requests.
Set login attempt limits.
Reduce how many failed attempts are allowed before a lockout or alert is triggered.
Monitor login activity.
Work with an MSP or IT partner (like AtNetPlus) who can watch for repeated or unusual attempts–especially after hours.
Next Steps: Ready to Strengthen Your MFA Strategy?
If you’re concerned about MFA fatigue or just want to be sure your authentication tools are doing their job— AtNetPlus is here to help.
Our team works with businesses across Akron, Canton, Cleveland, and Northeast Ohio to roll out modern MFA tools that reduce risk without frustrating your users. From setting up advanced options like number matching and biometric prompts, to training your team on what to watch for, we make the process seamless.
Let’s talk about what makes sense for your business. Whether you’re starting from scratch or improving what you already have, we’re here to help.
Schedule a quick consultation or contact us today to get started.
Sources:
- Legacy MFA from major airlines hacked, exposing reams of data | Biometric Update
- SCATTERED SPIDER Exploits | Crowdstrike
Serving Akron, Canton, Cleveland, and beyond.
